VMware vSphere 5.1 is now available for download. This vSphere Upgrade guide describes how to upgrade VMware vSphere™ to version 5.1. To learn how to simplify and automate your datacenter upgrade, see the vSphere Update Manager Installation and Administration Guide. If you want to move to vSphere 5.1 by performing fresh installations that do not… Continue reading VMware vSphere 5.1 Upgrade Guide
Category: Whitepapers
Virtualization technology white papers
Best Practices for Monitoring Virtual Environments
Virtualization is unquestionably one of the biggest and most widespread trends in computing in the last decade. By separating different elements of the computing platform, users in a growing number of businesses have done away with the “one app, one server” model and moved to Virtual Machines (VMs) in order to fully realize the potential… Continue reading Best Practices for Monitoring Virtual Environments
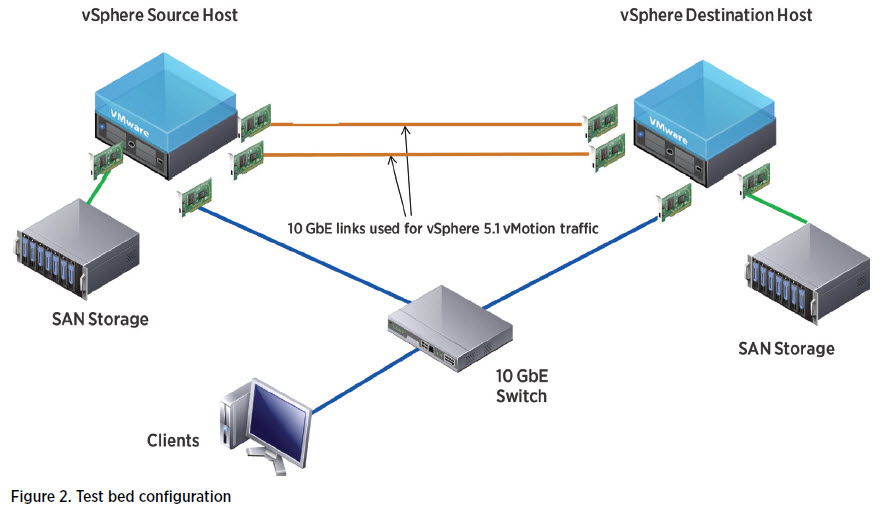
VMware vSphere 5.1 vMotion Architecture, Performance and Best Practices
A series of tests were conducted at VMware Performance labs to investigate and compare the performance implications of vSphere 5.1 vMotion over the proven vMotion and Storage vMotion technologies in various scenarios including the migration of a database server and an in-memory application. In addition, live migration tests were performed over metro area network scenarios.… Continue reading VMware vSphere 5.1 vMotion Architecture, Performance and Best Practices
Top 10 Cloud Backup and DR Best Practices
Building out a complete disaster recovery infrastructure can be cost prohibitive for many organizations. This paper identifies the many ways the public cloud can supplement backup and recovery strategies and offers overall best practices to ensure secure and efficient data protection. Many organizations want to improve their ability to recover from system failures and data… Continue reading Top 10 Cloud Backup and DR Best Practices
Top Considerations for Cloud, Virtualization and Security
Virtualization and cloud computing are all finding their way into today’s IT environments. More than before, small and medium enterprises are now looking into cloud and virtualization solutions to help meet business goals. With this new technological movement come some very important considerations to ensure optimal infrastructure efficiency. Security, sizing, management, and deployment methodologies must… Continue reading Top Considerations for Cloud, Virtualization and Security
Survey: Companies Still Struggling with Cloud Security
Globally, the cloud continues to pose challenges on how to deliver agile, yet secure, IT services to enterprises. The percentage of companies that reported a data security lapse or issue with their cloud service increased from 43 percent in 2011 to 46 percent in 2012, according to a recent global cloud security survey conducted by… Continue reading Survey: Companies Still Struggling with Cloud Security
Taking the Next Steps with Virtualization
Whether your organization is new to virtualization or you’ve been deploying it for years, the reality is that virtualization is a technology that should be a strategic part of your business, now and in the future. What are the use cases driving virtualization’s growth, and what are the important considerations – including hardware and software… Continue reading Taking the Next Steps with Virtualization
Overcoming the Storage Challenges of Virtual Desktops with Dell EqualLogic and Unidesk
Dell Desktop Virtualization Solutions (DVS) Enterprise Infrastructure Overview DVS Enterprise Infrastructure is designed and optimized to deliver a highly robust, highly scalable and highly available enterprise solution designed for implementations in sophisticated IT environments. The DVS Enterprise infrastructure implements enterprise scale virtualized servers, multi-tier virtual SAN storage and robust enterprise network architecture for multiple demanding… Continue reading Overcoming the Storage Challenges of Virtual Desktops with Dell EqualLogic and Unidesk