RSA, The Security Division of EMC® Corporation (NYSE: EMC), today announced new solutions within its Identity and Access Management (“IAM”) suite designed to address evolving security challenges that require new ways to manage and protect the growing number of users and device identities, the exponential growth in identity information and the need to help ensure… Continue reading RSA Unifies Identity and Access Management Across Cloud Infrastructures
Tag: access
UnboundID Debuts Cloud Identity Management Products based on SCIM Specification
UnboundID, a leading provider of identity data solutions for cloud, telco, and enterprise computing, today released the industry’s first commercially available products based on the Simple Cloud Identity Management (SCIM) standard. By supporting SCIM, UnboundID can provide a standardized and simpler solution for organizations provisioning and managing user identities across multiple cloud-based services, including IaaS,… Continue reading UnboundID Debuts Cloud Identity Management Products based on SCIM Specification
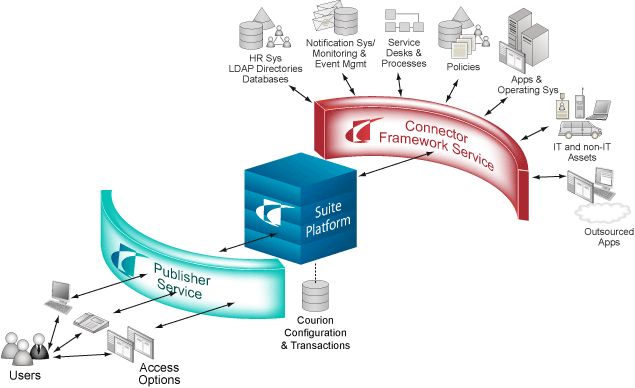
American Red Cross transitions to cloud computing platform, Deploys Access Risk Management Suite
Courion Corporation, the leader in identity and access management for access risk, today announced that the American Red Cross will use the Courion Access Risk Management Suite to streamline operations as part of an organization-wide transition to the Microsoft Office 365 cloud computing platform. The American Red Cross will use the Access Risk Management Suite… Continue reading American Red Cross transitions to cloud computing platform, Deploys Access Risk Management Suite