In Active Directory Federation Services there are two types of trusts. This video will look at the relying party trust which is configured on the account side. It essentially determines what information will be placed inside the claim.
Download the PDF handout
Trusts in AD FS
In this example ITFreeTraining has an Active Directory Federation Server and so does HighCost Training. On the ITFreeTraining side a relying party trust is created. The relying party trust is the configuration that is used to create a claim. It may seem that the relying party trust should be on the HighCost training side, however this is not possible. The reason for this is that ITFreeTraining creates a claim. Once this claim is created it cannot be changed. If the relying party trust was on the HighCost Training side, it would not be able to decide what data is in the claim as the claim would have already been created.
Relying Party Trust
A relying party trust is the configuration that is used in the accounts partner organization that is used to create claims. Normally it is used between the accounts partner and the resource partner but can also be used with a claims based application. When a relying party trust is created there are 3 rules that can be configured. These are, issuance transform rules, issuance authorization rules, and delegation authorization rules.
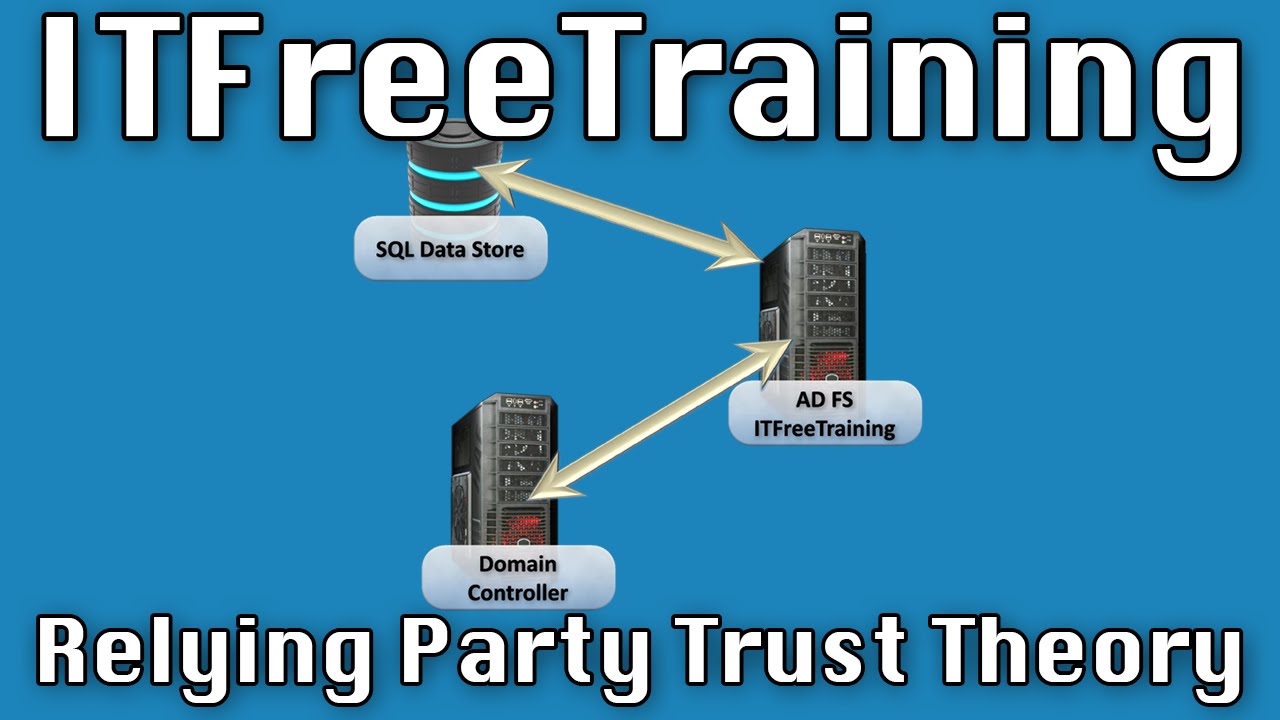
Relying Party Trust Example
In this example, an AD FS server is required to authenticate from a domain controller and obtain information from a SQL data store. When a claim is created, the AD FS federation server needs to be able determine where to get this data and which Domain Controller to authenticate with and how to output the data. In order to do this, 3 different types of rules are used. The issuance authorization rule determines how authentication will occur. In this case a domain controller is being used, however authentication could be as simple as the user having an e-mail address. Issuance transform rules define the data that is obtained and also define how it can be changed. For example, if the data obtained from the SQL Data Store was an e-mail address that ended in local, the transform rule may be defined to change this address to one ending in .com. Delegation authorization allows different users to be defined to access data. For example, delegation could be used for one user to obtain data for another user.
Issuance Transform Rules
In this example the job title is being added to the claim. A rule is created which defines that the job title should be obtained from an attribute store, most likely an SQL database. Once this data is obtained the job title is added to the claim. The problem is that some users do not have a job title and the claim cannot be used without a job title. The application that accepts this claim does not use the job title information in any way, however something needs to be configured, otherwise the claim will be rejected. To get around this, a second transform rule is created that configures the job title to “ITFreeTraining Employee” when no data is configured. This means that there will always be a value configured for the job title. You can see how transform rules can obtain and change data. Multiple rules can be stacked together in order to obtain the required result.
Delegation Authorization Rules
This rule essentially allows a user to be impersonated, that is, they are pretending to be someone else. In this example, the user obtains a claim from an AD FS server. They then use this claim to access a web server. The web server will then access a claim aware application using a different user name. So essentially they are performing the access as a different user than what was originally used in the claim.
Description to long for YouTube. Please see the following link for the rest of the description.
See or for our always free training videos. This is only one video from the many free courses available on YouTube.
References
“The Role of Claim Rules”
“Claims Transformation and Custom Attribute Stores in Active Directory Federation Services 2”
“When to Use Identity Delegation”